What is a side-channel attack?
A side channel attack is an exploit that preys on the information leaked from the minute details of the computer system rather than finding issues in the actual algorithm. Side channel attacks make use of timing, electromagnetic emissions, and power, which are the most common. But it is also possible to use the temperature or sound of a computer system to figure out information about it.
Problem Introduction:
The most common example is the concept of brute forcing a passcode. Assume that only the numbers 0–9 can be inputted into it. A standard brute force can get the answer in O(10^n) time. With some extra analysis and precision, it is possible to get the correct passcode in linear time. Checking whether the inputted passcode is right or not is where all of the information comes from. To check whether a given passcode is correct, each index is checked with its corresponding one. Refer to the following image: Assume “1234567” is the correct password for the remainder of this article.
Most of the implentations follow the following method: Each indicie is looped through, and whenever an indice doesn’t match, it immediately returns false, as it is now impossible for it to be the correct answer. If someone is asked to implement a basic passcode checker, the following code is basically guaranteed:
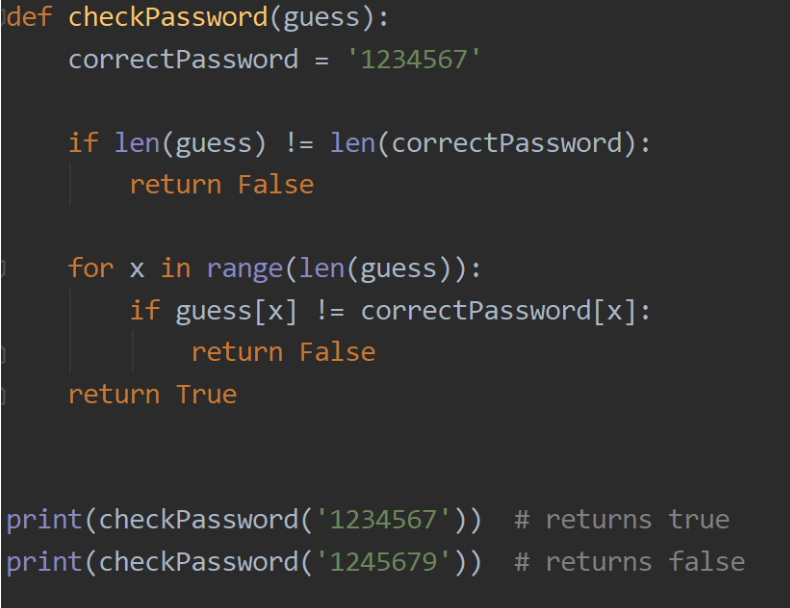
However, there is some information that is leaked from this implementation. Most people see the time it takes to do one iteration of the for loop as negligible. With enough precision, the microsecond difference between characters allows us to track our progress. Since it exits instantly, there is a time difference between when “1234568” is put in and “2345679” is put in. In the first input, the string will go through seven comparisons and fail on the last. While the second input will only compare once and fail on that first chance. It takes roughly seven times longer for the first input to run than the second. The differences are in microseconds (millionths of a second), but they are still noticeable with accurate tools. Refer to the following code:
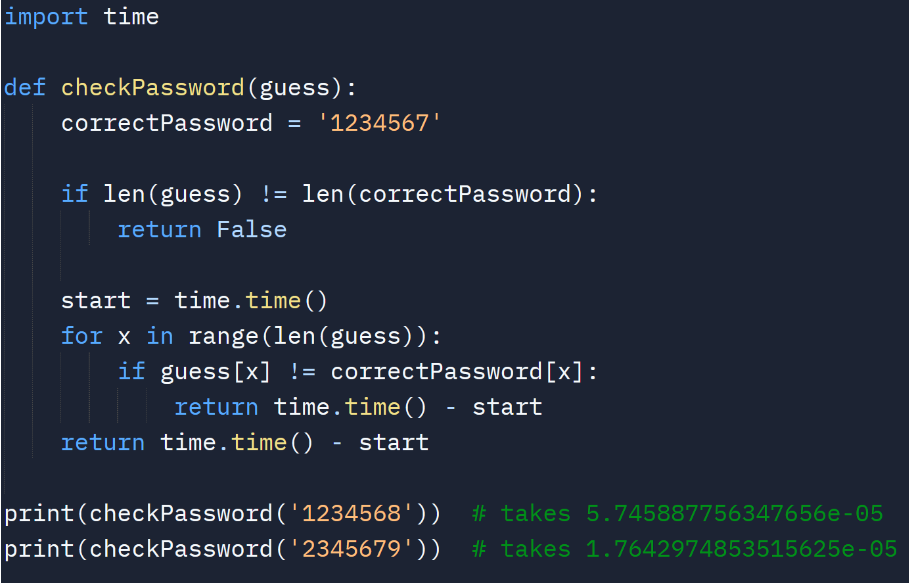
Now numbers can be guessed one by one. How long the code takes to be run can be used to confirm if any progress towards the correct passcode has been made. The longer it takes to run, the more likely it is going deeper into the for loop. So, it is closer to the passcode. For each index, starting from the beginning, each of the ten numbers has to be checked. The character addition that makes the current passcode take the longest time to run is most likely closer to the answer. This process will continue until all of the indicators have been checked, leaving you with the passcode that is most likely closest to the answer.
This can be expanded to other small factors like heat or electromagnetic emissions.
https://www.youtube.com/watch?v=D1DNz5sNDgE