Ethernet and Switches
Initially, phone calls would be made by connecting wires on a switchboard. Only once the wires were connected could any communication occur. This process wasn’t automated and had to be done manually by someone. A little later than that, humans were tasked with solving the problem of how computers should be hooked up. This article will discuss Ethernet, which is when different components are all connected through a physical medium. The two original ways of connecting all of the computer hardware were the following: Ring topology (left) and bus topology (right)
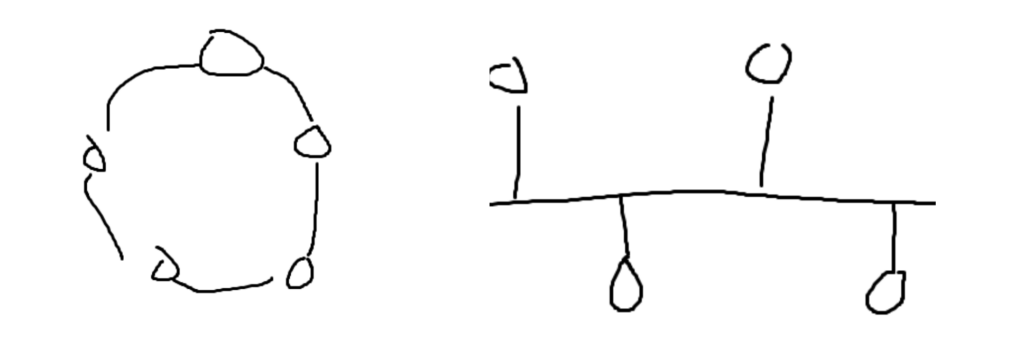
Both bus and ring topologies ran into the same issues. Both only supported half-duplex. This meant that a component could not send and receive information at the same time. Keeping the system all together was also an issue. As there was only one path in the system, if that wire were to break, it would completely separate the system.
There was also the possibility of a collision. This is when two requests are made at the same time. When traveling through the wires, information collides and becomes jumbled. The requests are forced to be sent again, which decreases the overall performance of the system.
Ethernet
MAC addresses were mentioned at an earlier time. A MAC address is burned onto the network card, and it is used as the permanent unique identifier of a computer. MAC addresses are always 48 bits long and are written in hexadecimal (base 16). Below is how an Ethernet is constructed.
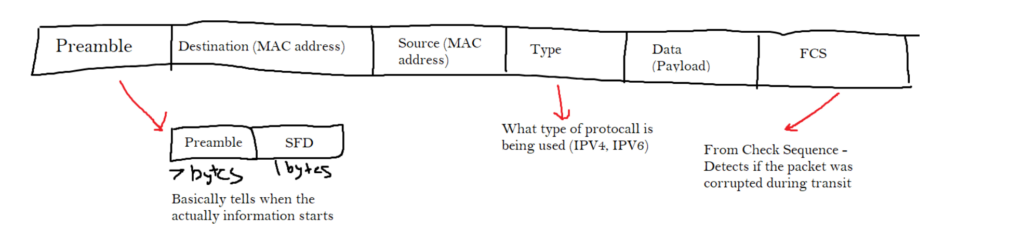
Special MAC addresses:
Broadcast: Sent to everyone in the local system. ffff.ffff.ffff
Multicast: Sent to a specific group baed on there properties. Example: 0100.0CCC.CCCC
Bridges (Divide and Conquer)
Some issues with hubs are that all devices are in the same collision domain. It is also half-duplex, and when data is sent, it has to go to every device. A bridge is a physical object that fixes some of the issues.
Instead of existing as one big system, it will be broken up into smaller pieces. All of the smaller pieces will be connected in the middle by a bridge.
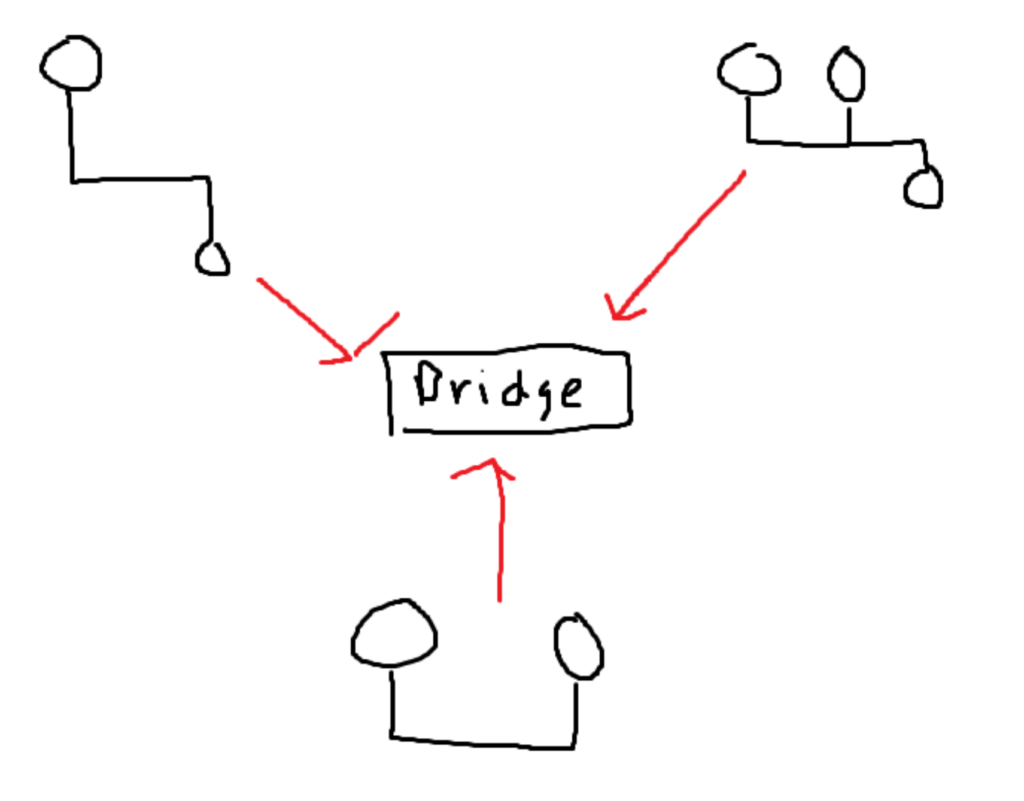
Bridges remember all of the MAC addresses on the system. On top of remembering the MAC addresses, it is also important to remember which group each of the MAC addresses belongs to.
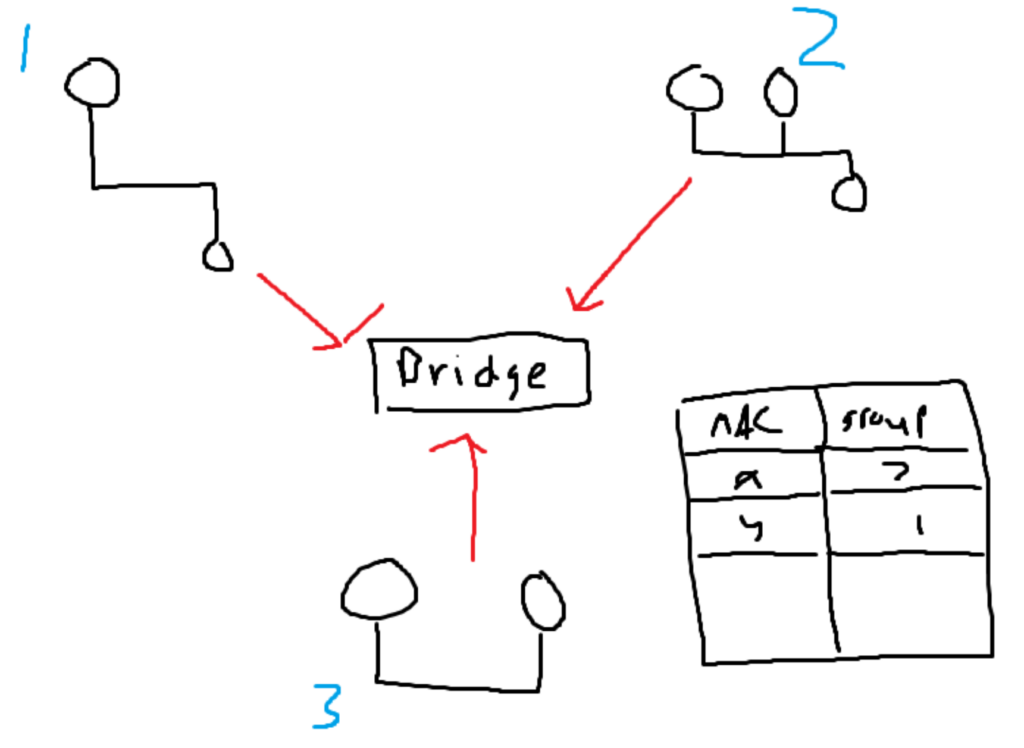
Each request will go to the bridge. If the destination MAC address is in a different section, the bridge will forward the request. Now it will be given to all of the devices in the destination segment. If the MAC address is in the same segment, the bridge will not forward the information, and the request will be sent to everyone in the current segment.
Bridges create smaller collision domains and prevent flooding. Initially, bridges do not have all of the MAC addresses memorized. When a value is requested that isn’t in the bridge, it is forced to send a message to everyone in the system asking where the destination is located. It will record the MAC addresses in its cache as they come in.
It’s also important to mention that the values inside the bridge cache are mutable. If a computer is moved from Section 1 to Section 2, the information is now false and has to be changed. Whenever the bridge detects incorrect information, it will adjust accordingly.
Bridge Cache Timer:
There might be a lot of computers on the network. So, the bridge also has a way of keeping its cache small and optimized. If someone plugs in a guest computer, it will have a spot on the table. It’s not very efficient to keep the computer there even when it is not connected to the system.
So, each value in the bridge cache is on a timer. If that item is either requested or requested, the timer is reset. If the timer reaches zero, then it is wiped from the cache.
Switches (The Modern Stuff):
Switches are the tools that are currently in use in modern times. Switches are able to take advantage of hubs and bridges and put them together. Instead of a bus topology like the hub, switch to a star topology.
Switches similar to bridges are also intelligent. They will record MAC addresses. In the case of the start topology, every single device is part of its own collision domain. Thus making collisions even more rare. Instead of half duplex, these networks are now full duplex, meaning that devices can send and receive at the same time.
Here are a couple of methods that switches use to deal with traffic:
Store and Forward (Safety): When receiving information, the switch will wait until it has the entire frame of information. It will do an error check and then pass the frame on.
Cut Through (fastest): The switch will wait until it sees the destination MAC address. Once it sees the destination, it immediately forwards the rest of the frame.
Fragment-Free (middle ground): The first 64 bits of the frame are the most likely to contain errors. If there aren’t any issues in the first 64 bits, the entire frame will be forwarded instantly.
Most of the time, the methods that a switch will use to conduct traffic are determined by the manufacturer.